Dec 11, 2024 Information hub
Understanding Information Disclosure Vulnerabilities: Risks & Fixes
Information disclosure vulnerabilities, often overlooked, can be a treasure trove for attackers. These vulnerabilities expose sensitive information, such as user data, business logic, or technical details about an application. While the disclosed data might seem harmless initially, it often serves as a key to unlock further, more severe exploits. In this article, we’ll explore the basics of information disclosure, real-world examples, lab-based scenarios, and prevention techniques to fortify your systems against such risks.
What is Information Disclosure?
Information disclosure, also known as information leakage, happens when a system unintentionally exposes sensitive data to unauthorized entities. This vulnerability often occurs due to misconfigurations, inadequate error handling, or careless coding practices. The exposed information can range from user data to critical application configurations, providing attackers with valuable insights into the system.
Common Examples of Leaked Information
User Data:
- Usernames, email addresses, passwords (even hashed ones), and financial information.
Business Secrets:
- API keys, database credentials, internal IP address, and environment variables.
Technical Details:
- Software versions, stack traces, debug information, and system configurations.
Why is This Dangerous?
Attackers exploit disclosed information to:
- Identify vulnerabilities: Knowledge of outdated software versions or exposed API keys can be directly leveraged for attacks.
- Plan precise exploits: Information like debug messages or error logs reveals how the application processes inputs, allowing attackers to craft targeted payloads.
- Expand the attack surface: Each piece of leaked information potentially uncovers additional entry points for exploitation.
Example in Action
Consider a web application revealing detailed error messages in response to invalid input. An attacker might learn:
- The database type (e.g., MySQL, PostgreSQL).
- The software framework and version used (e.g., Apache Struts 2).
- The exact point of failure, which can guide further exploitation.
Understanding these risks emphasizes the importance of securing systems against information disclosure vulnerabilities.
How Do Information Disclosure Vulnerabilities Arise?
- Careless Coding Practices:
Developers leaving behind comments, hard-coded secrets, or debug features in production.
- Improper Configuration:
Failing to disable verbose error messages, debug modes, or default settings.
- Flawed Application Logic:
Applications returning distinct responses to invalid inputs, enabling attackers to enumerate data.
Real-World Examples
Revealing Directory Structures
- Misconfigured robots.txt files exposing hidden directories.
- Unprotected backup files accessible from public URLs.
Verbose Error Messages
- Database table names revealed in error responses.
- Stack traces exposing software versions or configurations.
Hard-Coded Sensitive Data
- API keys or credentials left in the source code.
Subtle Hints Through Behavior
- Applications behaving differently when queried with valid vs. invalid resources or usernames.
Lab Scenarios: Learning Through Practice
Lab 1: Information Disclosure in Error Messages
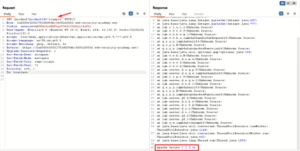
Scenario: A verbose error message reveals the framework version in use.
Solution:
- Use Burp Suite to inspect responses for error messages.
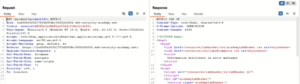
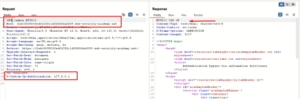
- Send invalid input to a parameter, e.g., GET /product?productId=”example”.
- Extract the version number from the stack trace.
Outcome: The attacker learns the application is using Apache Struts 2.3.31, which might have known vulnerabilities.
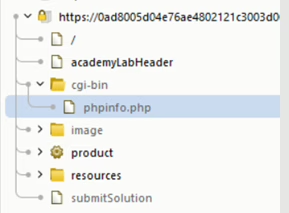
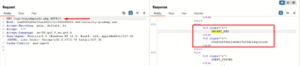
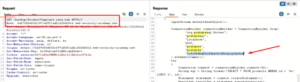
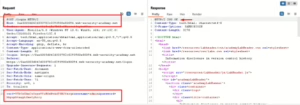
Lab 2: Information Disclosure on Debug Pages
Scenario: A debug page reveals sensitive details like the SECRET_KEY environment variable.
Solution:
- Explore website and create site map in burp.
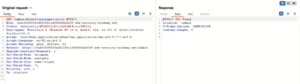
- Send /cgi-bin/phpinfo.php request into repeater tab and make a request.
- Access the debug page and extract the SECRET_KEY.
Outcome: Sensitive details disclosed due to an exposed debug page.
Lab 3: Source Code Disclosure via Backup Files
Scenario: A backup file in a hidden directory contains hard-coded credentials.
Solution:
- Inspect /robots.txt to find the /backup directory.
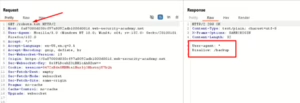
- Access /backup/ProductTemplate.java.bak to retrieve source code.
- Extract the database password from the code.
Outcome: Hard-coded database credentials are revealed.
Lab 4: Authentication Bypass via Information Disclosure
Scenario: An admin interface authentication relies on a custom HTTP header.
Solution:
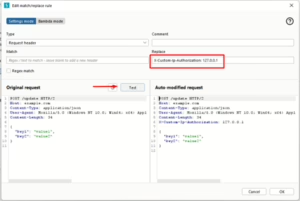
- Use the TRACE method on /admin page to uncover the X-Custom-IP-Authorization header.
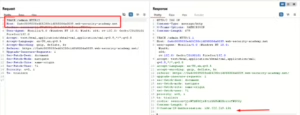
- Modify requests to include X-Custom-IP-Authorization: 127.0.0.1 for bypassing authentication.
- Add “X-Custom-Ip-Authorization: 127.0.0.1” in match/replace rule, and click test to test rule.
- Now make delete user request from the admin panel.
Outcome: Authentication is bypassed using disclosed header information.
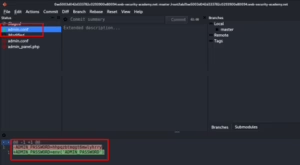
Lab 5: Information Disclosure in Version Control History
Scenario: A leaked Git repository reveals a previously hard-coded admin password.
Solution:
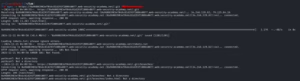
- Open web and browse to /.git, you will observe Git Version.
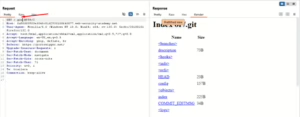
- Download .git data using tools like wget.
- Inspect commit history for sensitive changes (e.g., admin password replaced with environment variable).
- Use the old password to log in as an admin and perform actions.
Outcome: Access gained through poor version control practices.
Impact of Information Disclosure
Information disclosure vulnerabilities might seem low-risk at first glance, but their repercussions can be far-reaching. They can cause immediate harm or lay the groundwork for more significant attacks. Here’s a closer look:
Direct Impact
- Financial Loss:
Sensitive financial information like credit card details, billing information, or bank credentials may be leaked. Attackers can exploit this data for unauthorized transactions or identity theft.
- Reputation Damage:
Breaches involving confidential business or user data can severely harm a company’s credibility, leading to customer attrition and loss of stakeholder trust.
- Legal Consequences:
Failure to protect sensitive information can result in hefty fines under regulations like GDPR, HIPAA, or PCI DSS.
Indirect Impact
- Attack Surface Expansion:
-
- Exposed technical details such as stack traces, server configurations, or API endpoints provide attackers with a roadmap for exploiting other vulnerabilities.
-
- Leaked user information, such as usernames or email addresses, can facilitate credential-stuffing attacks.
- Enabling High-Severity Attacks:
-
- Attackers often chain disclosed information with other vulnerabilities to launch more advanced attacks, such as privilege escalation or lateral movement within networks.
-
- For instance, exposed software version details can be matched with known exploits in public vulnerability databases, accelerating attack execution.
- Competitive Disadvantage:
Competitors gaining access to proprietary algorithms, source code, or business plans through disclosure can result in significant losses in market position.
Real-Life Examples of Impact
- Equifax Data Breach (2017):
-
- Exposed personal data of 147 million individuals, including Social Security numbers.
-
- Cost the company over $1.4 billion in settlements and damages.
- GitHub Token Leak:
-
- In many incidents, API tokens and secrets have been accidentally pushed to public repositories, allowing attackers unauthorized access to systems.
- Sony Pictures Hack (2014):
-
- Information disclosure through emails and sensitive files led to massive public embarrassment and financial damage.
Understanding these impacts underscores the necessity of proactive measures to detect and mitigate information disclosure vulnerabilities before they can be exploited.
Preventing Information Disclosure
Preventing information disclosure requires a combination of secure coding practices, awareness, and robust infrastructure configurations. Below are actionable measures to minimize the risks associated with this vulnerability:
- Educate Your Team
-
- Training Programs:
Conduct regular training sessions to help developers, testers, and operations teams identify sensitive information and learn secure handling techniques.
- Training Programs:
-
- Awareness of Best Practices:
Share guidelines on secure coding, including proper input validation and output encoding.
- Awareness of Best Practices:
-
- Threat Modeling:
Incorporate threat modeling sessions to anticipate potential data leakage scenarios during development.
- Threat Modeling:
- Code Audits and Automation
-
- Automated Tools:
Use static application security testing (SAST) tools to identify debug comments, hard-coded credentials, and other sensitive data in the code.
- Automated Tools:
-
- CI/CD Pipelines:
Integrate tools like GitHub Advanced Security or TruffleHog to scan for secrets before deployment.
- CI/CD Pipelines:
-
- Manual Reviews:
Supplement automated processes with manual code reviews to identify overlooked vulnerabilities.
- Manual Reviews:
- Generic Error Messages
-
- Error Handling:
-
-
- Replace verbose error messages with user-friendly yet non-descriptive messages like:
“An error occurred. Please try again later.”
- Replace verbose error messages with user-friendly yet non-descriptive messages like:
-
-
-
- Log detailed error messages securely in server logs, accessible only by authorized personnel.
-
- Secure Configurations
-
- Disable Debug Modes:
Ensure that debug and diagnostic tools are disabled in production environments.
- Disable Debug Modes:
-
- Audit Third-Party Integrations:
Review third-party libraries and frameworks to disable or remove unnecessary features that could expose information.
- Audit Third-Party Integrations:
-
- Least Privilege Principle:
Configure systems to limit access based on roles, ensuring that sensitive data is only accessible when necessary.
- Least Privilege Principle:
- Version Control Hygiene
-
- Avoid Sensitive Data in Repositories:
-
-
- Use environment variables or secure vaults (e.g., HashiCorp Vault, AWS Secrets Manager) for sensitive configurations instead of hardcoding them.
-
-
- Audit Git History:
Regularly scan commit histories using tools like git-secrets or Gitleaks to identify and remove exposed secrets.
- Audit Git History:
-
- Proper .gitignore Files:
Ensure .gitignore files exclude sensitive directories or files, such as .env, from being committed.
- Proper .gitignore Files:
Additional Best Practices
- Monitor and Test Regularly:
Perform routine penetration testing to identify potential information disclosure risks.
- Content Security Policies (CSP):
Implement CSPs to mitigate information leaks through browser-based attacks like XSS.
- Secure APIs:
-
- Validate and sanitize input/output in APIs to avoid accidental disclosure.
-
- Implement authentication and rate limiting.
- Data Minimization:
Only collect and store data that is absolutely necessary. Regularly review and purge outdated or unnecessary information.
Adopting these preventive measures reduces the likelihood of information disclosure, protecting both users and organizations from significant risks.
Conclusion
Information disclosure vulnerabilities, while seemingly benign, can be the stepping stone for attackers to breach systems. Through practical examples and real-world lab scenarios, this article highlights the significance of identifying and mitigating such leaks. By adopting secure development practices, robust configurations, and regular audits, organizations can minimize the risk of information disclosure, fortifying their applications against potential exploits.
Whether you’re a pentester or a developer, mastering the nuances of information disclosure is a vital skill in today’s cybersecurity landscape.