Oct 25, 2024 Information hub
SQL Injection: A Detailed Technical Overview
SQL Injection (SQLi) is one of the most common, widespread and dangerous web security vulnerabilities in web applications. It allows attackers to interfere with the queries that applications make to their databases. This can result in unauthorized access, data modification, or even full system compromise. SQLi can lead to data breaches, allowing attackers to retrieve sensitive information like passwords, credit card numbers, and user details. In this article, we delve deep into the types of SQL injection attacks, real-world examples, their impact, and the necessary mitigations to prevent such attacks.
Types of SQL Injection Attacks
SQL Injection attacks come in various forms, each leveraging different techniques to exploit vulnerabilities. In some situations, an attacker can escalate a SQL injection attack to compromise the underlying server or other back-end infrastructure. It can also enable them to perform denial-of-service attacks. Below are some of the main types of SQLi attacks:
1. Error-Based SQL Injection
Error-based SQL injection relies on generating database errors that can be useful for attackers to understand the structure of the database. By manipulating the query, attackers force the database to return error messages containing sensitive information.
For example:
URL: https://insecure-website.com/products?id=1′
SQL Query: SELECT * FROM products WHERE id = ‘1’
If the database responds with an error message, attackers can use that information to craft further attacks.
2. Blind SQL Injection
Blind SQL injection occurs when the application does not return any direct output from the database, but attackers can infer information by observing changes in the behavior or responses of the application. There are two subtypes:
2.1 Boolean-Based Blind SQL Injection
In Boolean-based blind SQLi, attackers use true/false conditions to determine the validity of a query. The application behavior changes depending on the Boolean condition.
For example:
URL: https://insecure-website.com/products?id=1′ AND 1=1 — [Valid query]
URL: https://insecure-website.com/products?id=1′ AND 1=2 — [Invalid query]
By observing changes in the application’s responses (e.g., page loading or error or Length), attackers can infer whether the condition is true or false.
2.2 Time-Based Blind SQL Injection
In Time-based blind SQLi, attackers inject queries that trigger a time delay in the response. This technique helps determine whether a condition is true or false by causing the database to pause execution.
For example:
URL: https://insecure-website.com/products?id=1′ AND IF(1=1, SLEEP(5), 0) — [Pauses execution for 5 seconds]
If the page response is delayed, it indicates the condition was true, allowing attackers to extract information through time delays.
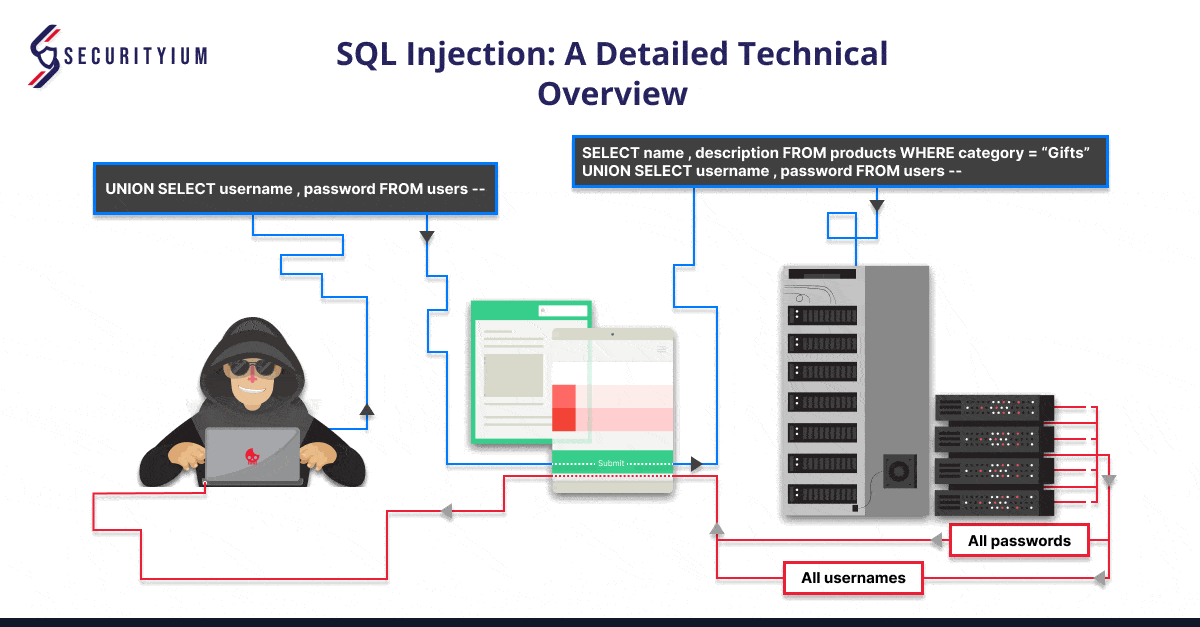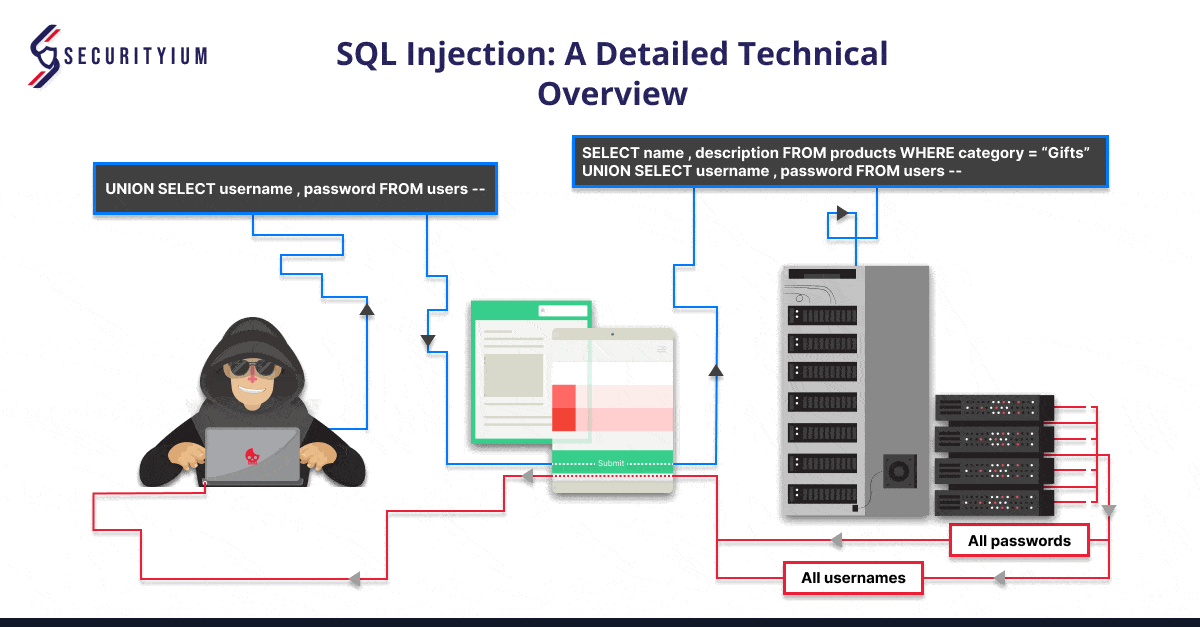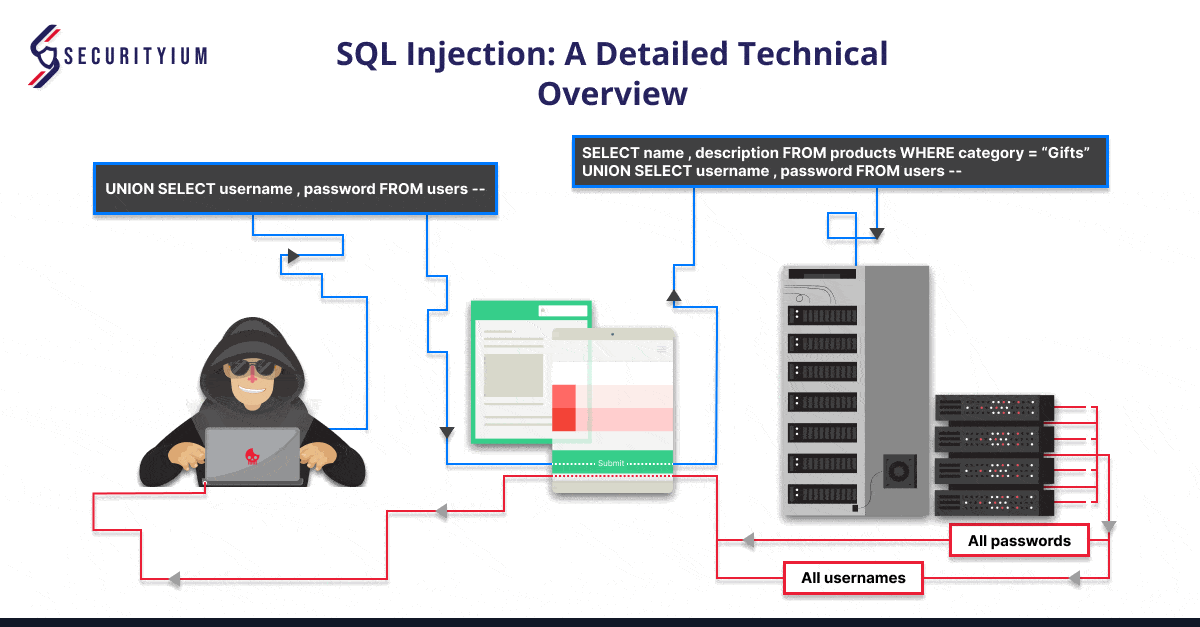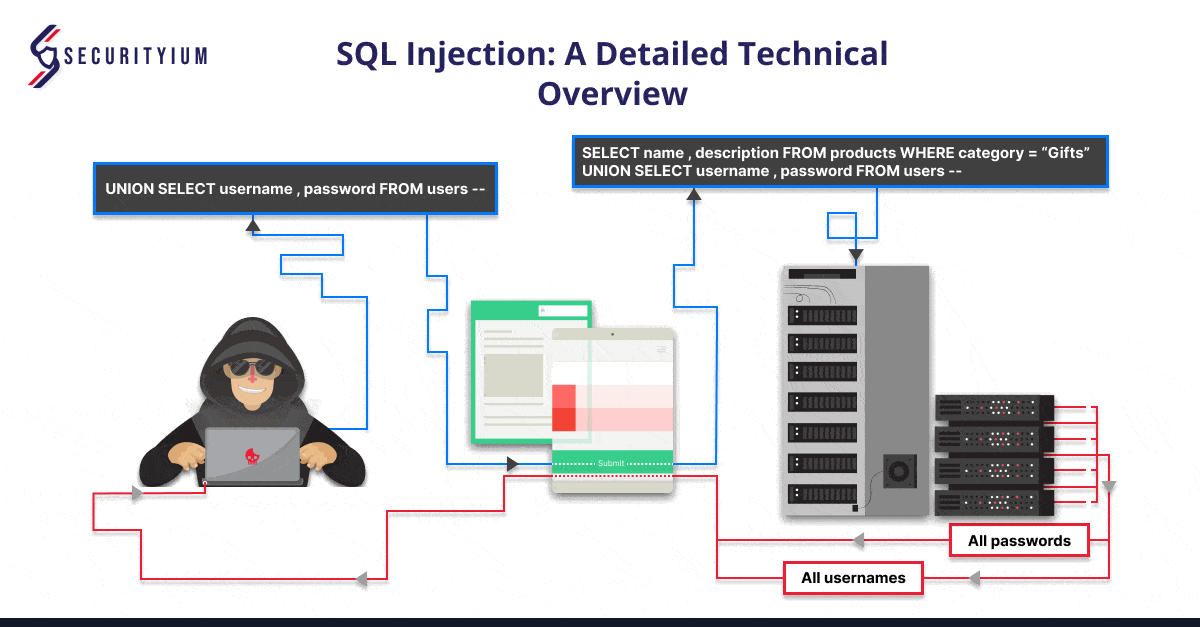
3. UNION-Based SQL Injection
UNION-based SQL injection allows attackers to retrieve data from other tables by appending the results of one query to another using the UNION keyword.
For example:
If an application executes the following query containing the user input Gifts:
SELECT name, description FROM products WHERE category = ‘Gifts’
An attacker can submit the input:
‘ UNION SELECT username, password FROM users–
This causes the application to return all usernames and passwords along with the names and descriptions of products.
URL: https://insecure-website.com/products?id=1 UNION SELECT username, password FROM users –
4. Out-of-Band SQL Injection
Out-of-band SQL injection occurs when attackers use alternative channels to retrieve data, such as DNS requests. This technique is useful when the database server is not directly connected to the web application, or the responses are not visible. Attackers inject queries that trigger network interactions (e.g., DNS or HTTP) to exfiltrate data.
Real-World SQL Injection Example
1. HackerOne SQL Injection Vulnerability (2023)
In 2023, a security researcher discovered a SQL injection vulnerability in the HackerOne platform, which is used by hackers and security professionals to report bugs. The vulnerability was found in the admin interface of the platform. By exploiting the SQL injection flaw, the attacker was able to access sensitive information stored in the database, such as user details and bounty-related data. HackerOne quickly patched the vulnerability and awarded the researcher with a bounty for their discovery.
2. Indian Government’s Covid-19 Database Breach (2021)
In early 2021, the Covid-19 vaccine registration portal run by the Indian government experienced a major security breach due to a SQL injection vulnerability. Attackers exploited the flaw to access the personal data of millions of Indian citizens, including names, contact details, and Aadhaar (identity) numbers. The breach posed significant privacy risks and highlighted the importance of securing government digital infrastructures against SQLi attacks.
Impact of SQL Injection Attacks
The impact of a successful SQL injection attack can range from minor information leakage to complete system compromise. Common consequences include:
- Unauthorized access to sensitive data, such as usernames, passwords, and financial information.
- Data corruption or deletion, leading to system downtime or permanent loss of data.
- Installation of persistent backdoors into the system, enabling long-term exploitation.
- Breaches that result in legal and regulatory fines, along with reputational damage to the affected organization.
Remediation and Prevention of SQL Injection
Preventing SQL injection attacks requires proper coding practices and defensive measures:
- Use Parameterized Queries (Prepared Statements): This is the most effective way to prevent SQLi attacks. It ensures that user input is treated as data rather than part of the query structure.
- Use ORM (Object Relational Mapping) Libraries: ORM libraries like Hibernate or Entity Framework automatically handle query generation, reducing the risk of SQLi
- Implement Input Validation: Validate and sanitize all user inputs, ensuring that they conform to expected formats and values.
- Least Privilege Principle: Limit database privileges for users and applications. Do not allow database users to have access beyond what is necessary.
- Web Application Firewalls (WAF): Deploy WAFs that can detect and block common SQL injection attacks by analyzing HTTP requests.
Conclusion
SQL injection continues to be a significant threat in web application security. By understanding the various types of SQLi attacks, real-world implications, and implementing proper prevention techniques, developers can mitigate this risk. Employing a defense-in-depth approach, including secure coding practices, input validation, and the use of prepared statements, can drastically reduce the risk of SQL injection vulnerabilities.
