



Securityium identified a critical XSS vulnerability, labelled as CVE-2015-6540, in Intellect Core banking software, allowing attackers to execute harmful JavaScript code. Immediate action is needed to mitigate this threat.

In cybersecurity, mere compliance with industry standards is no longer sufficient to protect your organization from the m.

Securityium uncovered critical vulnerabilities in Synology's systems, including unauthenticated file uploads and an SSRF flaw, highlighting the need for continuous vigilance and proactive cybersecurity measures.

Securityium identified a vulnerability in certain Netgear routers, officially labeled as CVE-2021-29069. This flaw, rooted in insufficient validation within the email module, exposes affected devices to severe command injection attacks.
Multiple pentesting vendors enhances security by finding diverse vulnerabilities, ensuring frequent testing, optimizing resources, and gaining a competitive edge through bakeoffs.

Penetration testing, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web and mobile application security, penetration testing is commonly used to uncover vulnerabilities.

In the modern digital era, the banking industry heavily relies on technology and interconnected systems to provide efficient and convenient financial services to customers. However, this reliance on technology also exposes the banking sector to various cyber threats
Discover how to enhance your GoLang code security with comprehensive checks and validations from the Go Secure Coding Practices Guide. Learn about key areas like input validation, output encoding, authentication, and more.
Enhance your software security and ensure compliance with Securityium's Software Composition Analysis (SCA) services. Identify and address security flaws, licensing compliance issues, and code quality concerns related to open source software.

In the fast-evolving digital landscape, the realm of cybersecurity continues to face ever-changing challenges. As technology advances, so do the methods and sophistication of cyberattacks.


The human element remains both the greatest advantage and the most critical weakness in the continuously growing field of cybersecurity. As business leaders and key decision-makers, your role in steering your organisation toward success is undeniable.
The need for effective defense measures has never been more vital in the ever-changing landscape of cybersecurity, where threats continue to grow in complexity and frequency.

Ony compliance with industry standards is no longer sufficient to protect your organization from the multifaceted threats that lurk in the digital shadows.

Explore VAPT’s transformative journey from risk to resilience with Securityium, uncovering vulnerabilities, fortifying defenses, and achieving robust cybersecurity.

Explore the evolving threatscape and learn how Securityium helps you adapt your cybersecurity strategy to stay ahead of cyber threats and protect your digital assets.

Uncover how Penetration Testing fortifies cybersecurity. See how Securityium identifies vulnerabilities and strengthens your digital defenses for proactive protection.
Explore the vital role of penetration testing in safeguarding sensitive data across diverse industries and mitigating risks of data exposure in today's digital landscape.
Penetration testing (pentesting) is crucial for strengthening IT infrastructure against cyber threats by simulating attacks and identifying vulnerabilities.
Prevent data breaches with Securityium's insights on phishing risks, breach causes at Dropbox, and proactive cybersecurity measures.
Protect your business from phishing attacks with Securityium's insights on preventing cyber threats through robust IT security measures and training.
Protect your business from supply chain attacks with Securityium's comprehensive strategies and insights on mitigating cybersecurity risks effectively.

An Incremental Penetration Test is an approach of security testing that focuses specifically on evaluating the security of new or modified features in an application since the last full penetration test.
Enhance your cybersecurity with attack surface scanning. Discover vulnerabilities, safeguard digital assets, and ensure compliance. Explore our blogs for such proactive strategies.
Learn about CVE-2024-43381, a Stored XSS vulnerability in reNgine. This article covers how the flaw works, its potential risks, and key strategies to mitigate the threat.
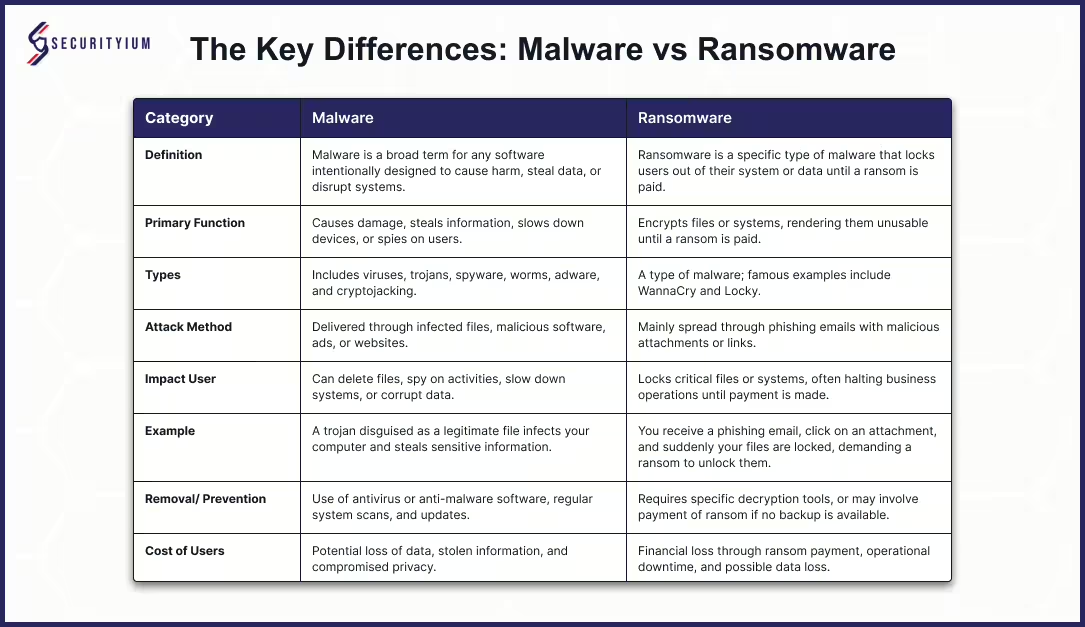
Learn the differences between malware and ransomware, their attack methods, and effective prevention strategies to safeguard your data.
Explore the distinctions between viruses, worms, and Trojan horses in this guide. Understand how each operates, with examples, and learn essential cybersecurity tips for staying protected.
Discover how GDPR affects small businesses, key compliance steps to follow, and the long-term benefits of data protection. Ensure your business meets GDPR standards and builds customer trust.
This guide on GDPR for small businesses explains its importance, challenges, and simple steps to comply with data privacy laws, safeguarding your business from fines and protecting customer data.
Discover why compliance with GDPR is crucial in 2025. Learn practical steps to protect personal data, avoid hefty fines, and build trust with your customers.
Discover practical ways businesses can comply to GDPR, understand its importance, and explore the benefits of adhering to data privacy regulations for better security and customer trust.
Explore data protection compliance, the laws businesses must follow, and steps to ensure secure data management. Learn how staying compliant can protect your business and customers' trust.
This GDPR checklist outlines key steps for businesses to ensure data protection compliance, from consent and data audits to security measures, helping avoid fines and protect customer data.
Discover the crucial GDPR compliance requirements your business must follow to protect data, avoid penalties, and build customer trust. A guide to help ensure compliance in 2025.
Learn about essential GDPR requirements, including data minimization, lawful processing, and data breach notifications, to help businesses stay compliant and safeguard personal data.
Discover the importance of GDPR compliance in today's world, practical tips for ensuring data protection, and how businesses can stay ahead in the evolving privacy landscape.
Discover the key steps to GDPR compliance with our General Data Protection Regulation checklist. Stay compliant, avoid fines, and enhance customer trust with simple, actionable tips.
Discover how to be GDPR compliant with actionable steps. Ensure your business protects personal data and meets legal requirements to avoid penalties and enhance customer trust.
Explore the key differences between pen test vs vulnerability scan. Learn how each method can strengthen your organization's cybersecurity strategy against evolving threats.
Explore the differences between penetration testing vs vulnerability scanning. Learn how both methods work together to enhance your organization's cybersecurity posture.
Discover the key benefits of Vulnerability Assessment and Penetration Testing for organizations. Enhance your cybersecurity strategy and prevent data breaches effectively.
Learn about the role of a graduate pentester London, the skills required, current trends, and how to thrive in this growing cybersecurity field. Discover your path to success today!
Discover the world of penetration tester jobs, essential skills, and current trends in cybersecurity. Learn how to build a successful career in this high-demand field.
Learn about penetration tester jobs in the UK, including skills, responsibilities, and future trends. Explore why this role is crucial in today's cybersecurity landscape.
Learn about penetration testing methodology, its steps, and importance in today’s cybersecurity landscape. Discover how it helps protect against threats and improve security.
Learn about the importance of a security test in today’s digital world. Explore different types of tests and how they help protect your systems and data from cyber threats effectively.
Find out how a web app pentest helps secure your online apps. Discover and fix weaknesses to protect your data and improve your overall security.
Learn how app security is vital for protecting sensitive data, maintaining user trust, and preventing costly breaches. Discover common threats and effective solutions for safeguarding apps.
Explore the significance of application security in today’s digital landscape. Learn about common threats, effective strategies, and future trends to enhance your application's safety and integrity.
Explore the importance of a DAST scan in modern cybersecurity. Understand how it identifies vulnerabilities, protects web applications, and keeps your business safe from cyber threats.
Discover the importance of DAST testing in identifying vulnerabilities in web applications. Ensure your organization's security and compliance with effective DAST testing strategies.
Discover how DAST tools improve your web security. They find weaknesses early to help prevent costly cyberattacks and keep you safe and compliant with rules.
Understand why Dynamic Application Security Testing is crucial for web apps. It finds security problems, helping businesses defend against cyber threats and stay compliant.
Learn about Dynamic Application Security Testing tools and their importance in today’s cybersecurity landscape. They help find security issues early, protecting your applications from attacks.
Discover the benefits of a sast scan for detecting vulnerabilities in applications. Improve security, save costs, and protect sensitive data effectively.
SAST testing analyzes source code to identify vulnerabilities before deployment. Learn its benefits, current trends, and how it secures software in today's digital landscape.
Discover how Static Application Security Testing (SAST) identifies vulnerabilities early in the development process, helping organizations enhance security and comply with regulations.
In today's digital age, website safety is crucial. Explore free tools and tips to check website safety, safeguard your personal information, and enjoy a secure online experience.
Learn how URL scanners work to identify harmful links, prevent phishing attacks, and safeguard your online presence, making them vital for individuals and businesses in today's digital world.

Discover essential Docker Security Best Practices that help protect your containerized applications by using trusted images, setting resource limits, and managing permissions.
