Oct 22, 2024 Information hub
Pentest Report: It’s Importance in Strengthening Cybersecurity
In today’s digital age, cybersecurity is no longer a luxury but a necessity. With the increasing number of cyberattacks, businesses and organizations are more vulnerable than ever. One of the most effective ways to assess and improve an organization’s security posture is through penetration testing (pentesting). However, the true value of a pentest lies not just in the testing itself but in the pentest report that follows.
A pentest report is a comprehensive document that outlines the findings of a penetration test, including vulnerabilities, risks, and recommendations for remediation. It serves as a roadmap for organizations to understand their security weaknesses and take actionable steps to mitigate them. In this blog post, we will dive deep into the significance of a pentest report, its structure, and how it can help businesses stay ahead of cyber threats.
Why Pentest Reports Matter in Today’s Cybersecurity Landscape
The Growing Threat of Cyberattacks
Cyberattacks are becoming more frequent, sophisticated, and damaging. According to a report by Cybersecurity Ventures, cybercrime is expected to cost the world $10.5 trillion annually by 2025. This alarming statistic highlights the urgent need for organizations to proactively identify and address vulnerabilities before they can be exploited by malicious actors.
Penetration testing is a proactive approach to cybersecurity that simulates real-world attacks on an organization’s systems, networks, and applications. However, the true value of a pentest lies in the pentest report, which provides a detailed analysis of the test’s findings and offers actionable recommendations for improving security.
The Role of a Pentest Report
A pentest report is not just a technical document; it is a strategic tool that helps organizations:
- Identify vulnerabilities: The report highlights weaknesses in the organization’s security infrastructure that could be exploited by attackers.
- Assess risk: The report provides a risk assessment, helping organizations prioritize which vulnerabilities to address first based on their potential impact.
- Guide remediation efforts: The report offers recommendations for fixing vulnerabilities and improving overall security.
- Demonstrate compliance: Many industries are subject to regulatory requirements (e.g., GDPR, HIPAA, PCI-DSS) that mandate regular security assessments. A pentest report can serve as evidence of compliance with these regulations.
The Structure of a Pentest Report
A well-structured pentest report is essential for ensuring that the findings are clear, actionable, and easy to understand. While the exact structure may vary depending on the organization and the scope of the test, most pentest reports follow a similar format. Below is a breakdown of the key sections typically found in a pentest report.
1. Executive Summary
The executive summary is the most important section for non-technical stakeholders, such as executives and board members. It provides a high-level overview of the pentest, including:
- Scope of the test: What systems, networks, or applications were tested?
- Objectives: What were the goals of the pentest (e.g., identify vulnerabilities, assess risk)?
- Key findings: A summary of the most critical vulnerabilities discovered during the test.
- Risk assessment: An evaluation of the overall risk to the organization based on the findings.
- Recommendations: A brief overview of the recommended actions to address the vulnerabilities.
The executive summary should be concise and written in non-technical language to ensure that all stakeholders can understand the key takeaways.
2. Methodology
The methodology section provides a detailed explanation of how the pentest was conducted. This section is important for technical teams who need to understand the testing process and validate the findings. Key elements of the methodology section include:
- Testing approach: Was the test conducted using a black-box, white-box, or gray-box approach?
- Tools used: What tools and techniques were used to identify vulnerabilities (e.g., Nmap, Metasploit, Burp Suite)?
- Testing phases: A breakdown of the different phases of the test, such as reconnaissance, vulnerability scanning, exploitation, and post-exploitation.
- Limitations: Any limitations or constraints that may have affected the test results (e.g., time constraints, scope limitations).
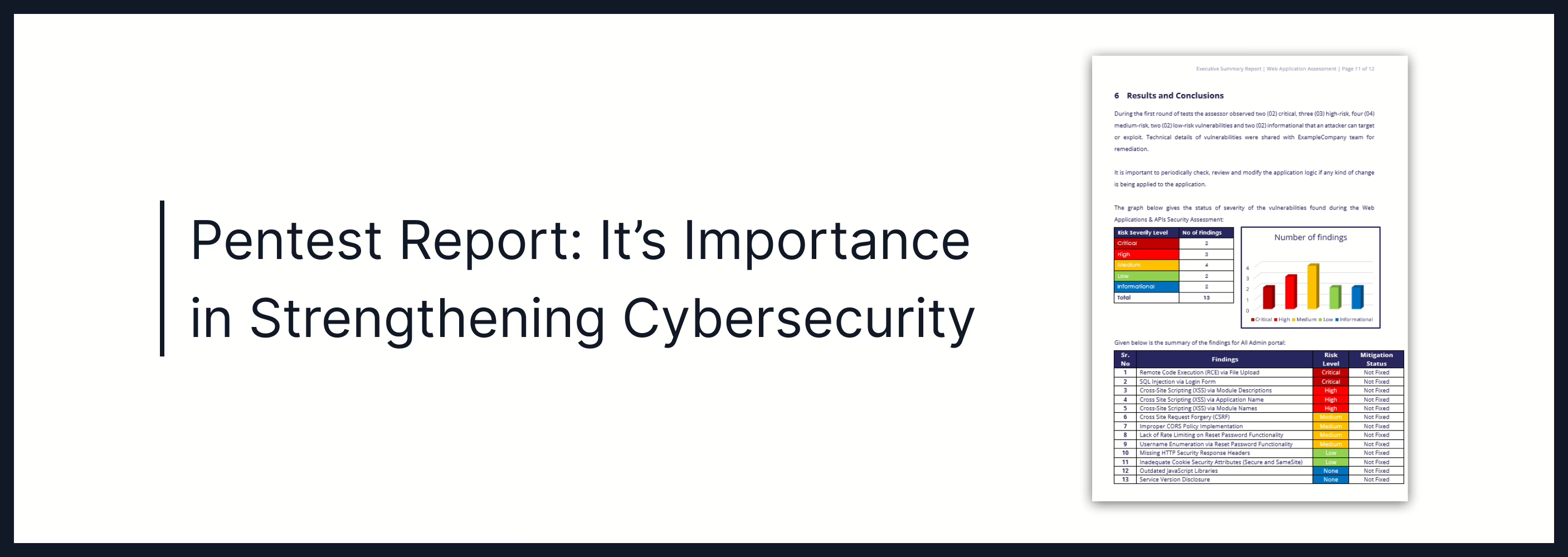
3. Findings
The findings section is the heart of the pentest report. It provides a detailed analysis of the vulnerabilities discovered during the test, along with their potential impact and recommendations for remediation. This section is typically divided into the following subsections:
a. Vulnerability Description
For each vulnerability, the report should include a clear and concise description of the issue. This should include:
- Vulnerability name: The name or type of vulnerability (e.g., SQL injection, cross-site scripting).
- Affected systems: A list of the systems, networks, or applications that are affected by the vulnerability.
- Technical details: A detailed explanation of how the vulnerability works and how it was discovered.
b. Risk Assessment
Each vulnerability should be assigned a risk rating based on its potential impact and likelihood of exploitation. Common risk rating systems include:
- CVSS (Common Vulnerability Scoring System): A widely used framework for assessing the severity of vulnerabilities.
- Custom risk ratings: Some organizations may use their own risk rating system based on factors such as business impact, data sensitivity, and exploitability.
c. Proof of Concept (PoC)
In some cases, the pentest report may include a proof of concept (PoC) to demonstrate how the vulnerability can be exploited. This can help the organization’s technical team understand the severity of the issue and prioritize remediation efforts.
d. Recommendations
For each vulnerability, the report should provide clear and actionable recommendations for remediation. This may include:
- Patching: Applying security patches or updates to fix the vulnerability.
- Configuration changes: Modifying system or network configurations to mitigate the risk.
- Code fixes: For application vulnerabilities, the report may recommend specific code changes to address the issue.
4. Risk Assessment and Prioritization
Not all vulnerabilities are created equal. Some may pose a significant risk to the organization, while others may be less critical. The risk assessment and prioritization section helps organizations understand which vulnerabilities should be addressed first.
This section typically includes:
- Risk matrix: A visual representation of the vulnerabilities based on their severity and likelihood of exploitation.
- Prioritization: A list of vulnerabilities ranked in order of priority, with high-risk vulnerabilities at the top.
5. Remediation Plan
The remediation plan provides a roadmap for addressing the vulnerabilities identified in the pentest. This section should include:
- Timeline: A recommended timeline for addressing each vulnerability based on its priority.
- Resources: Any additional resources or tools that may be needed to implement the recommended fixes.
- Monitoring and follow-up: Recommendations for ongoing monitoring and follow-up testing to ensure that the vulnerabilities have been successfully remediated.
6. Conclusion
The conclusion of the pentest report should summarize the key findings and recommendations. It should also emphasize the importance of ongoing security assessments and the need for a proactive approach to cybersecurity.
Practical Examples and Case Studies
To illustrate the importance of a pentest report, let’s look at a few real-world examples and case studies.
Case Study 1: Equifax Data Breach
In 2017, Equifax, one of the largest credit reporting agencies in the world, suffered a massive data breach that exposed the personal information of 147 million people. The breach was caused by a vulnerability in the company’s web application that had not been patched.
A thorough pentest report could have identified this vulnerability and provided recommendations for patching it before it was exploited by attackers. This case highlights the importance of regular penetration testing and the need for organizations to act on the findings of their pentest reports.
Case Study 2: Target Data Breach
In 2013, Target suffered a data breach that compromised the credit card information of 40 million customers. The breach was caused by a vulnerability in the company’s network that allowed attackers to gain access to sensitive data.
A pentest report could have identified this vulnerability and provided recommendations for securing the network. This case underscores the importance of conducting regular penetration tests and using the findings to improve security.
Current Trends and Challenges in Pentest Reporting
As the cybersecurity landscape continues to evolve, so too do the challenges and trends associated with pentest reporting. Some of the key trends and challenges include:
1. Automation in Pentesting
With the rise of automated pentesting tools, there is a growing trend toward using automation to streamline the pentesting process. While automation can help identify common vulnerabilities more quickly, it is not a replacement for manual testing. A comprehensive pentest report should include both automated and manual testing results to ensure that all potential vulnerabilities are identified.
2. Increasing Complexity of IT Environments
As organizations adopt new technologies such as cloud computing, IoT, and AI, their IT environments are becoming more complex. This complexity makes it more challenging to conduct thorough penetration tests and produce accurate pentest reports. Organizations must ensure that their pentest reports cover all aspects of their IT infrastructure, including cloud environments and third-party services.
3. Compliance Requirements
Many industries are subject to regulatory requirements that mandate regular security assessments. Pentest reports are often used to demonstrate compliance with these regulations. However, organizations must ensure that their pentest reports meet the specific requirements of their industry (e.g., PCI-DSS, HIPAA, GDPR).
Benefits of a Comprehensive Pentest Report
A well-executed pentest report offers numerous benefits to organizations, including:
- Improved security posture: By identifying and addressing vulnerabilities, organizations can significantly reduce their risk of a cyberattack.
- Regulatory compliance: A pentest report can help organizations meet regulatory requirements and avoid costly fines.
- Informed decision-making: The report provides valuable insights that can help organizations make informed decisions about their security investments.
- Enhanced reputation: Demonstrating a commitment to cybersecurity can enhance an organization’s reputation and build trust with customers and partners.
Conclusion
In today’s rapidly evolving cybersecurity landscape, a pentest report is an invaluable tool for organizations looking to protect their systems, data, and reputation. By providing a detailed analysis of vulnerabilities, risks, and remediation strategies, a pentest report helps organizations stay one step ahead of cyber threats.
To maximize the value of a pentest report, organizations should ensure that it is well-structured, easy to understand, and actionable. By acting on the findings of the report and implementing the recommended fixes, organizations can significantly improve their security posture and reduce their risk of a cyberattack.
Actionable Takeaways:
- Conduct regular penetration tests to identify vulnerabilities in your systems, networks, and applications.
- Ensure that your pentest report is comprehensive, well-structured, and easy to understand.
- Prioritize vulnerabilities based on their risk and potential impact, and develop a remediation plan to address them.
- Use the pentest report to demonstrate compliance with regulatory requirements and build trust with customers and partners.
- Stay informed about the latest trends and challenges in pentesting to ensure that your security assessments are up to date.
By following these best practices, organizations can use pentest reports to strengthen their cybersecurity defenses and protect themselves from the ever-growing threat of cyberattacks.
