With the ProSecurity Pentest Portal, manage all your Pentesting assessment reports in one secure location.
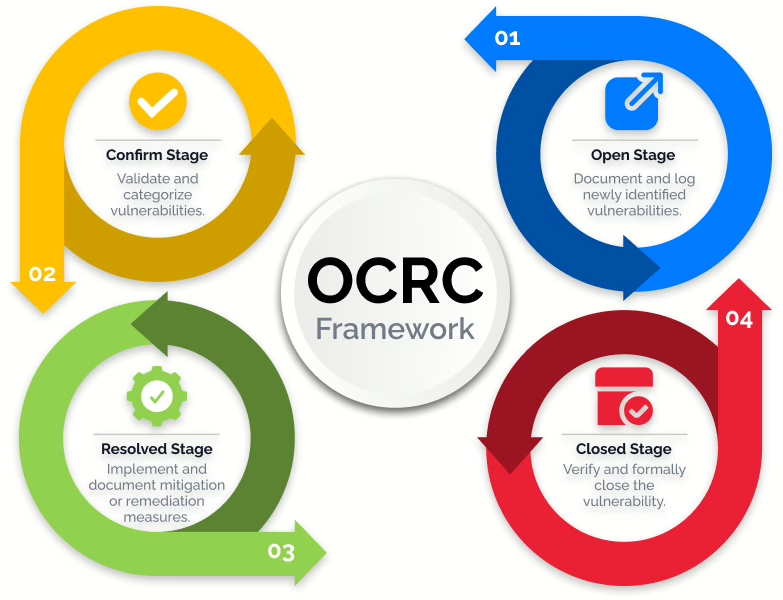
Streamline your pentesting process with our unique framework that simplifies and optimizes vulnerability tracking during penetration tests.
Reduce Your Security Assessment Costs with efficient approach to pen testing. Effective & efficient task management. Task list focused on your technology & system.

With Little to no effort, stay ahead in your compliance game with our compliance-ready reports, one report to meet most compliances (PCI-DSS, GDPR, HIPAA, etc.)
At Securityium, we're dedicated to transforming the way you experience security testing for your business. With over a decade of experience in IT security, we understand the complex challenges companies face—from managing skilled security teams and tracking vulnerabilities to handling multiple compliance reports across industry standards. Our solution acts as a streamlined, middle layer between testing frameworks and execution, driving efficiency, effectiveness, and organization while ultimately saving you time and reducing costs in your security testing process.
Our team of experts specializes in penetration testing and vulnerability assessments, serving hundreds of companies worldwide across diverse industries. Our innovative approach to security assessments delivers tailored, reliable, and efficient solutions designed to address your unique needs. We understand the challenges of today’s digital landscape and provide the expertise you need to navigate them with confidence. Explore Securityium's powerful solutions: Penetration Testing, IT Security Review & Assurance, and Enterprise Security Services. Each is crafted to strengthen your defenses, streamline compliance, and empower your business to tackle today’s evolving cyber threats head-on. Let us help you take security to the next level.
Penetration testing, often abbreviated as pentesting, is a crucial component of modern cybersecurity practices. It involves simulating real-world cyber attacks on a computer system, network, or application to identify vulnerabilities and weaknesses that malicious actors could exploit. By conducting pentests, organizations can proactively assess their security posture and take necessary measures to mitigate risks before they are exploited by attackers.
IT Security Review & Assurance involves the systematic examination and assessment of an organization’s information technology infrastructure, policies, and procedures to ensure that they are effective in protecting against cyber threats and meeting regulatory requirements. It encompasses various processes and practices aimed at maintaining the confidentiality, integrity, and availability of an organization’s data and systems.
Enterprise security refers to the comprehensive strategy and measures implemented by organizations to safeguard their digital assets, data, systems, networks, and users from cyber threats. In the modern business landscape, where digital technologies are ubiquitous and cyber attacks are increasingly sophisticated, ensuring robust enterprise security is paramount.

Securityium prioritizes manual testing to detect flaws that are missed by most automated scanners

Test custom exploits without disrupting with the operations of your business.

Adherence to compliance(s) by using our custom-tailored testing methodology & reports.

Customizable home grown scripts for scans that deliver accurate results.


Refined control over scans for traffic threshold, work transparency, and fine tuned scanners .

Easy to implement recommendations that cater to client’s business IT environment and use cases.

Two in-depth reports, one geared toward technical audience and the other toward executive audience.

Certified industry experts: CRTO, CRTP, LPT, CRT, CPSA , CISSP ,OSCP, OSCE.