Nov 6, 2024 Information hub
OWASP Web Top 10: Key Risks for Securing Web Apps
In today’s digital age, web applications are the backbone of many businesses, providing essential services to users worldwide. However, with the increasing reliance on web technologies comes the growing threat of cyberattacks. According to a report by Cybersecurity Ventures, cybercrime is expected to cost the world $10.5 trillion annually by 2025. This alarming statistic underscores the importance of securing web applications against potential vulnerabilities. One of the most trusted resources for web application security is the OWASP Web Top 10. The Open Web Application Security Project (OWASP) is a nonprofit organization that focuses on improving the security of software. Their OWASP Web Top 10 list is a regularly updated report that outlines the most critical security risks to web applications. This list serves as a guideline for developers, security professionals, and businesses to understand and mitigate the most common vulnerabilities in web applications.
In this blog post, we will explore the OWASP Web Top 10, its relevance in today’s cybersecurity landscape, practical examples of vulnerabilities, and how businesses can protect themselves from these threats.
What is the OWASP Web Top 10?
The OWASP Web Top 10 is a list of the most critical security risks to web applications, compiled by the OWASP community. It is updated periodically to reflect the evolving threat landscape and is widely regarded as the industry standard for web application security.
The list is based on data from various security organizations and includes input from security experts worldwide. Each risk is ranked based on its prevalence, detectability, and potential impact on businesses and users.
Why is the OWASP Web Top 10 Important?
The OWASP Web Top 10 is essential for several reasons:
- Industry Standard: It is recognized globally as a benchmark for web application security.
- Actionable Guidance: The list provides practical advice on how to mitigate each risk.
- Awareness: It helps developers and businesses understand the most common vulnerabilities and how to avoid them.
- Compliance: Many regulatory frameworks and security standards reference the OWASP Web Top 10, making it crucial for compliance.
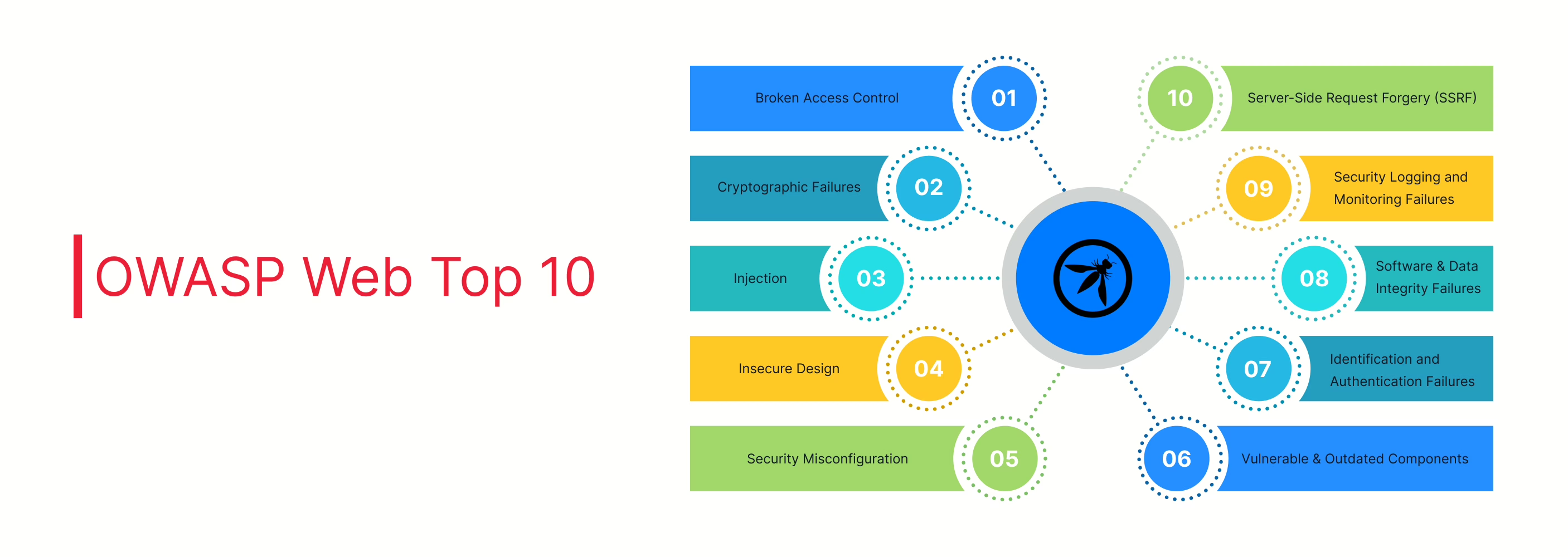
The OWASP Web Top 10: A Breakdown
Let’s dive into the OWASP Web Top 10 and explore each risk in detail, along with practical examples and solutions.
1. Broken Access Control
Broken Access Control occurs when users can access resources or perform actions that they should not be allowed to. This can lead to unauthorized access to sensitive data or functionality.
Example:
A common example is when a user can modify the URL to access another user’s account information. For instance, changing the URL from /user/123 to /user/124 might allow unauthorized access to another user’s data.
Solution:
- Implement proper role-based access control (RBAC).
- Use secure coding practices to ensure that access control checks are enforced on both the client and server sides.
2. Cryptographic Failures
Cryptographic failures occur when sensitive data is not properly protected through encryption. This can lead to data breaches, especially when sensitive information like passwords, credit card numbers, or personal data is exposed.
Example:
A website that stores passwords in plain text is vulnerable to cryptographic failures. If the database is compromised, attackers can easily access user credentials.
Solution:
- Use strong encryption algorithms (e.g., AES-256) for sensitive data.
- Ensure that data is encrypted both at rest and in transit.
- Regularly update cryptographic libraries to avoid known vulnerabilities.
3. Injection
Injection vulnerabilities occur when untrusted data is sent to an interpreter as part of a command or query. SQL injection is one of the most common types of injection attacks, where attackers can manipulate database queries to gain unauthorized access to data.
Example:
An attacker might input malicious SQL code into a login form, such as '; DROP TABLE users; --, which could delete the entire user database if the input is not properly sanitized.
Solution:
- Use parameterized queries or prepared statements to prevent SQL injection.
- Validate and sanitize all user inputs.
- Implement input validation on both the client and server sides.
4. Insecure Design
Insecure design refers to flaws in the architecture or design of an application that make it vulnerable to attacks. This can include poor security practices, lack of threat modeling, or failure to consider security during the design phase.
Example:
An application that does not enforce strong password policies (e.g., allowing weak passwords like “123456”) is an example of insecure design.
Solution:
- Incorporate security into the design phase of the software development lifecycle (SDLC).
- Perform threat modeling to identify potential risks early in the development process.
- Regularly review and update security policies.
5. Security Misconfiguration
Security misconfiguration occurs when security settings are not properly implemented or maintained. This can include default configurations, unnecessary features, or failure to apply security patches.
Example:
Leaving default credentials (e.g., admin/admin) on a web application is a common security misconfiguration that can lead to unauthorized access.
Solution:
- Regularly review and update security configurations.
- Disable unnecessary features and services.
- Apply security patches and updates promptly.
6. Vulnerable and Outdated Components
Using outdated or vulnerable components, such as libraries, frameworks, or plugins, can expose an application to security risks. Attackers often exploit known vulnerabilities in outdated components to gain access to systems.
Example:
The infamous Equifax breach in 2017 was caused by a vulnerability in the Apache Struts framework, which had not been updated.
Solution:
- Regularly update all components, including third-party libraries and frameworks.
- Use automated tools to scan for vulnerabilities in dependencies.
- Monitor security advisories for updates and patches.
7. Identification and Authentication Failures
Identification and authentication failures occur when an application does not properly verify the identity of users. This can lead to unauthorized access, account takeovers, or session hijacking.
Example:
An application that allows weak passwords or does not implement multi-factor authentication (MFA) is vulnerable to authentication failures.
Solution:
- Implement strong password policies and enforce MFA.
- Use secure session management practices, such as rotating session IDs after login.
- Regularly audit authentication mechanisms for vulnerabilities.
8. Software and Data Integrity Failures
Software and data integrity failures occur when an application does not properly protect against unauthorized changes to software or data. This can include tampering with code, data, or configuration files.
Example:
An attacker might modify a software update to include malicious code, which is then distributed to users.
Solution:
- Use digital signatures to verify the integrity of software updates.
- Implement checksums or hashes to detect tampering with data.
- Regularly audit software and data for integrity issues.
9. Security Logging and Monitoring Failures
Security logging and monitoring failures occur when an application does not properly log security events or monitor for suspicious activity. This can delay the detection of attacks and hinder incident response efforts.
Example:
A web application that does not log failed login attempts may fail to detect a brute-force attack.
Solution:
- Implement comprehensive logging for security-related events, such as login attempts, access control failures, and data modifications.
- Regularly monitor logs for suspicious activity.
- Use automated tools to detect and respond to potential security incidents.
10. Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) occurs when an attacker tricks a server into making requests to unintended locations, such as internal systems or external services. This can lead to data exfiltration, unauthorized access, or denial of service.
Example:
An attacker might exploit an SSRF vulnerability to access internal resources, such as a database or cloud metadata service, by sending a crafted request through the vulnerable server.
Solution:
- Validate and sanitize all user inputs that are used to generate server-side requests.
- Implement network segmentation to limit access to internal resources.
- Use allowlists to restrict outbound requests to trusted destinations.
The Relevance of OWASP Web Top 10 Today
The OWASP Web Top 10 remains highly relevant in today’s cybersecurity landscape. As web applications continue to evolve, so do the threats they face. The rise of cloud computing, microservices, and APIs has introduced new attack vectors, making it more important than ever to stay informed about the latest security risks.
Current Trends and Challenges
- Increased Use of APIs: As more businesses adopt APIs to connect services, API security has become a critical concern. Many of the risks in the OWASP Web Top 10, such as injection and broken access control, apply to APIs as well.
- Cloud Security: With the shift to cloud-based infrastructure, securing cloud environments has become a top priority. Misconfigurations in cloud services can lead to data breaches, as seen in several high-profile incidents.
- DevSecOps: The integration of security into the DevOps process (DevSecOps) is gaining traction. By incorporating security early in the development lifecycle, businesses can reduce the risk of vulnerabilities making it into production.
Future Developments
As technology continues to evolve, the OWASP Web Top 10 will likely be updated to reflect new threats. Some potential future developments include:
- AI and Machine Learning: As AI and machine learning become more prevalent, attackers may target these systems, leading to new types of vulnerabilities.
- Quantum Computing: The advent of quantum computing could render current encryption methods obsolete, necessitating new cryptographic standards.
Benefits of Implementing OWASP Web Top 10 Best Practices
By following the guidelines outlined in the OWASP Web Top 10, businesses can:
- Reduce the Risk of Data Breaches: Implementing proper security controls can prevent common vulnerabilities that lead to data breaches.
- Improve Compliance: Many regulatory frameworks, such as GDPR and PCI DSS, require businesses to implement security measures that align with the OWASP Web Top 10.
- Enhance Customer Trust: By securing web applications, businesses can protect customer data and build trust with their users.
- Save Costs: Preventing security incidents can save businesses the costs associated with data breaches, such as fines, legal fees, and reputational damage.
Conclusion
The OWASP Web Top 10 is an invaluable resource for anyone involved in web application development and security. By understanding and addressing the risks outlined in the list, businesses can significantly reduce their exposure to cyber threats and protect their users’ data.
To summarize, here are some actionable takeaways:
- Regularly review and update your web application’s security posture based on the OWASP Web Top 10.
- Implement strong access controls, encryption, and input validation to mitigate common vulnerabilities.
- Stay informed about emerging threats and trends in web application security.
- Incorporate security into every phase of the software development lifecycle (SDLC).
By prioritizing web application security and following the best practices outlined in the OWASP Web Top 10, businesses can stay ahead of cyber threats and ensure the safety of their digital assets.
