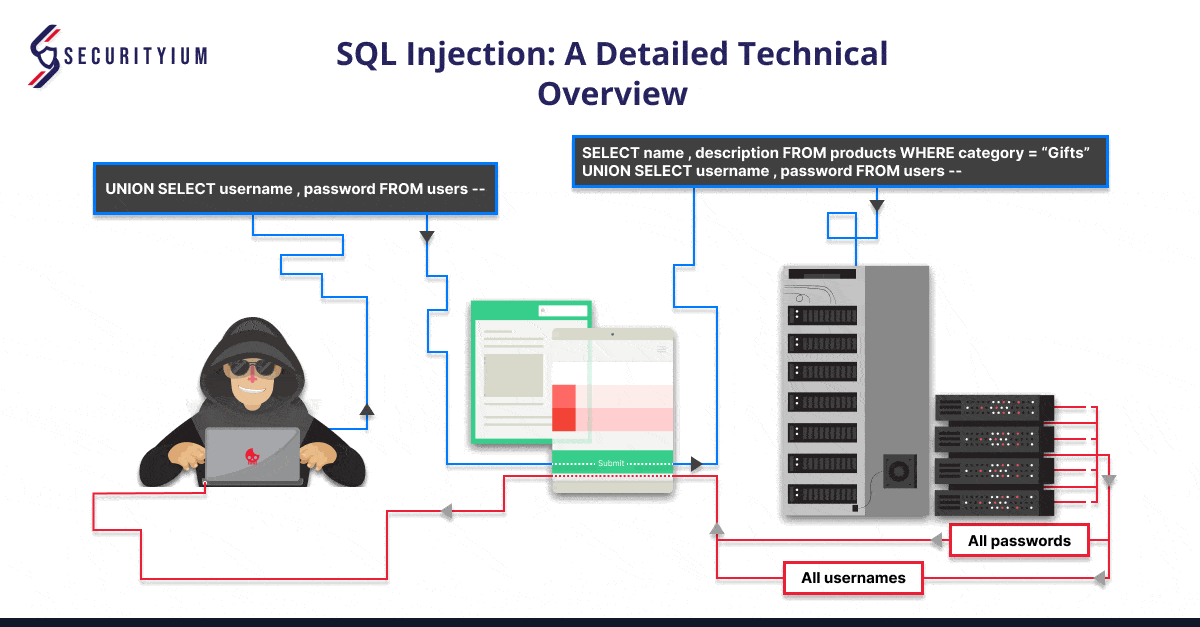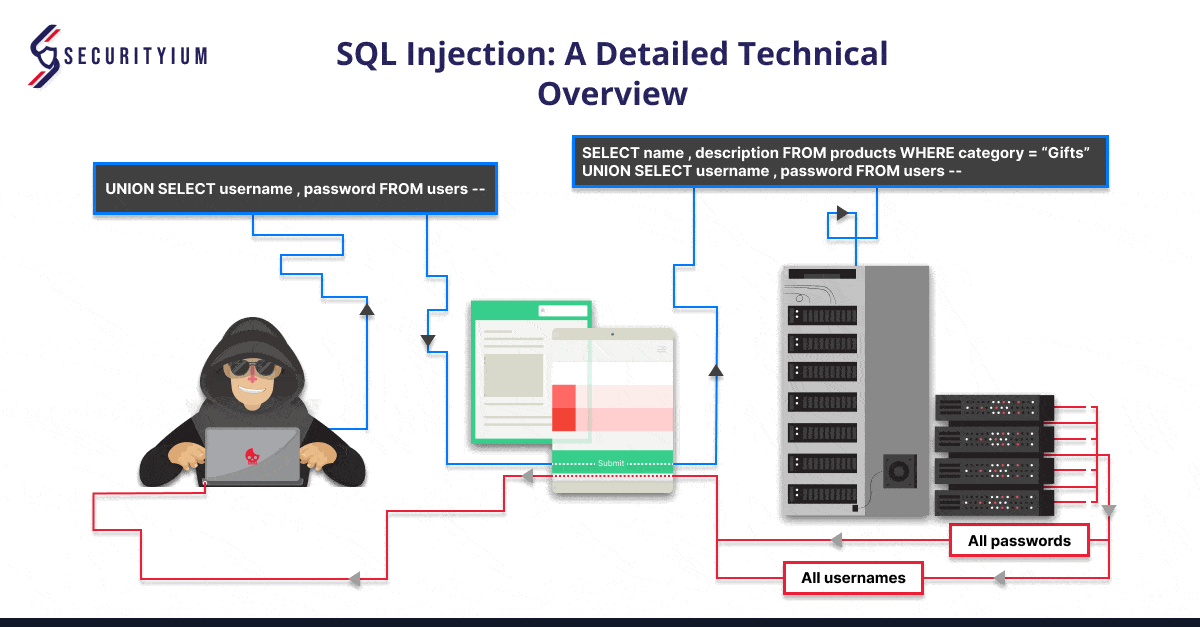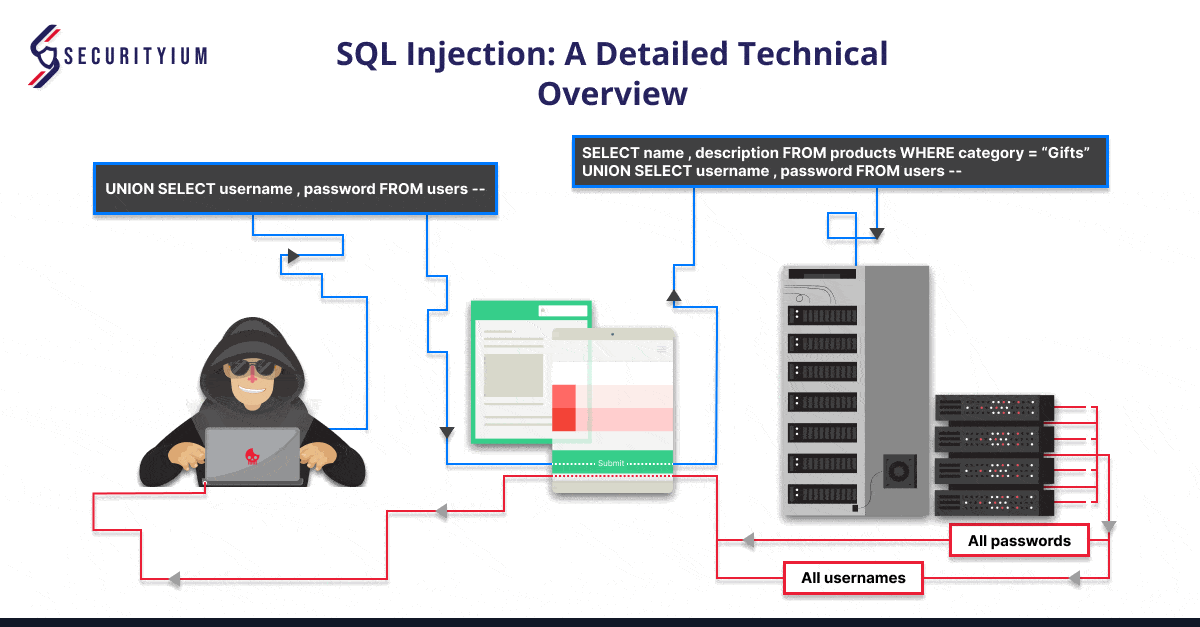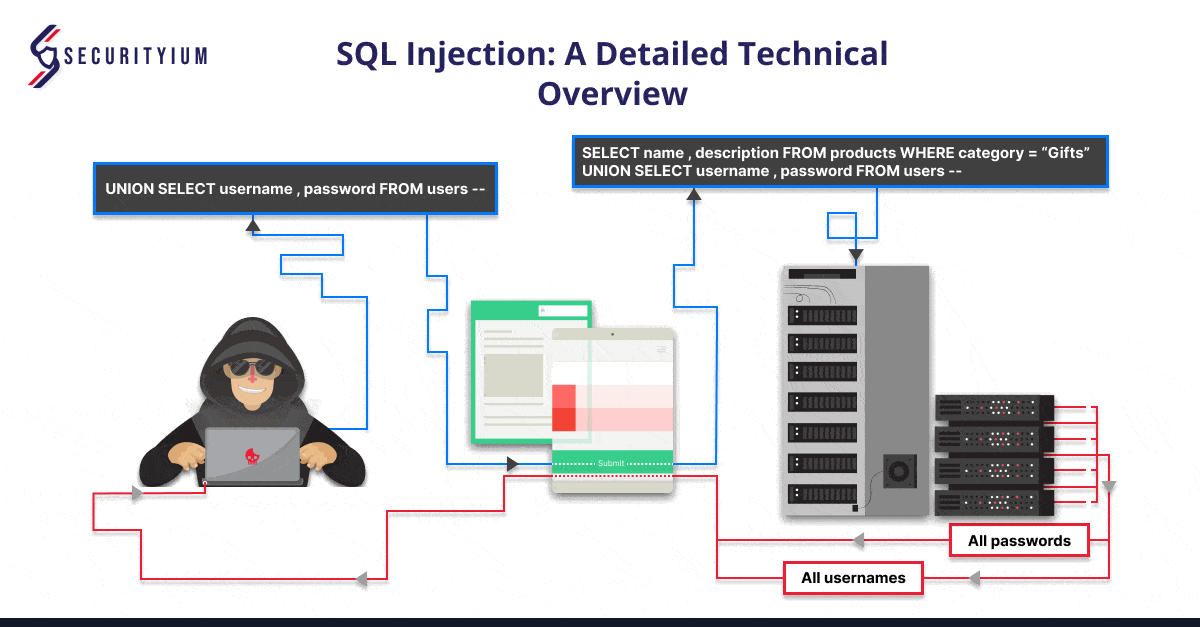
Categories
Recent Stories

Essential Security Testing Tools for Identifying and Reducing Cyber Risks
Nov 5, 2024 Information hub
Explore various security testing tools like SAST, DAST, and IAST, and learn how they help identify cyber risks, enhance compliance, and strengthen cybersecurity defenses.

The Importance of Application Security Testing
Nov 5, 2024 Information hub
Discover the importance of application security testing to secure data, avoid breaches, and comply with regulations. Learn key testing types and emerging trends.

15 Best Practices for Successful Network Penetration Testing
Nov 5, 2024 Information hub
Explore 15 essential network penetration testing practices to identify and fix vulnerabilities, strengthen defenses, and protect your network from cyber threats.

Top 12 Best Practices for Effective Web Application Pentesting
Oct 29, 2024 Information hub
Discover the top 12 best practices for web application pentesting to strengthen security, identify vulnerabilities, and protect your app from cyberattacks.

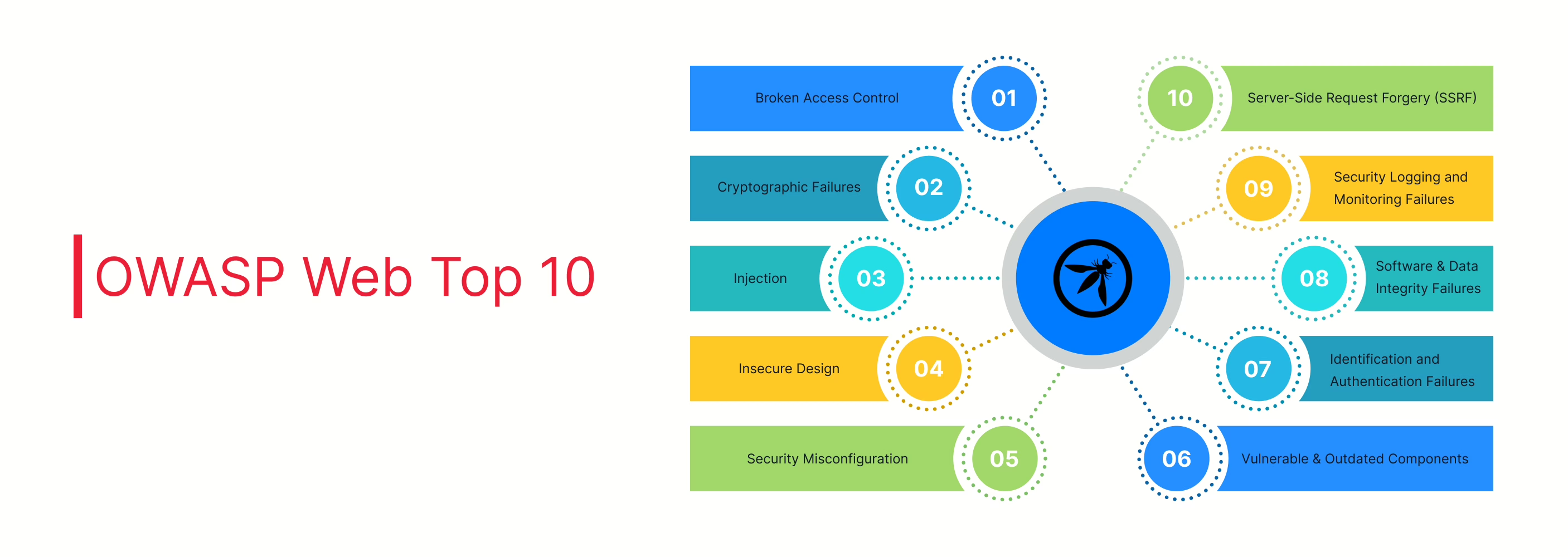
Understanding the Open Web Application Security Project (OWASP) Top Ten for Web App Security
Oct 25, 2024 Technical Write ups
Learn about the Open Web Application Security Project (OWASP) Top Ten, a key guide for tackling the most critical web app vulnerabilities. Follow best practices to reduce security risks and ensure data protection.

Essential Guide to OWASP Top 10
Oct 25, 2024 Information hub
Understand the OWASP Top 10 risks to web apps and how to secure against them. Discover the latest threats, compliance needs, and strategies to boost your web app security.
Why Application Programming Interface Security is Crucial?
Oct 25, 2024 Information hub
Explore why application programming interface security matters, the latest security challenges, and best practices to protect APIs from cyberattacks and ensure data safety.

Essential API Security Best Practices to Safeguard Your Data
Oct 25, 2024 Information hub
Discover API security best practices to shield data from threats. Learn practical strategies like strong authentication, encryption, and monitoring to secure your APIs.