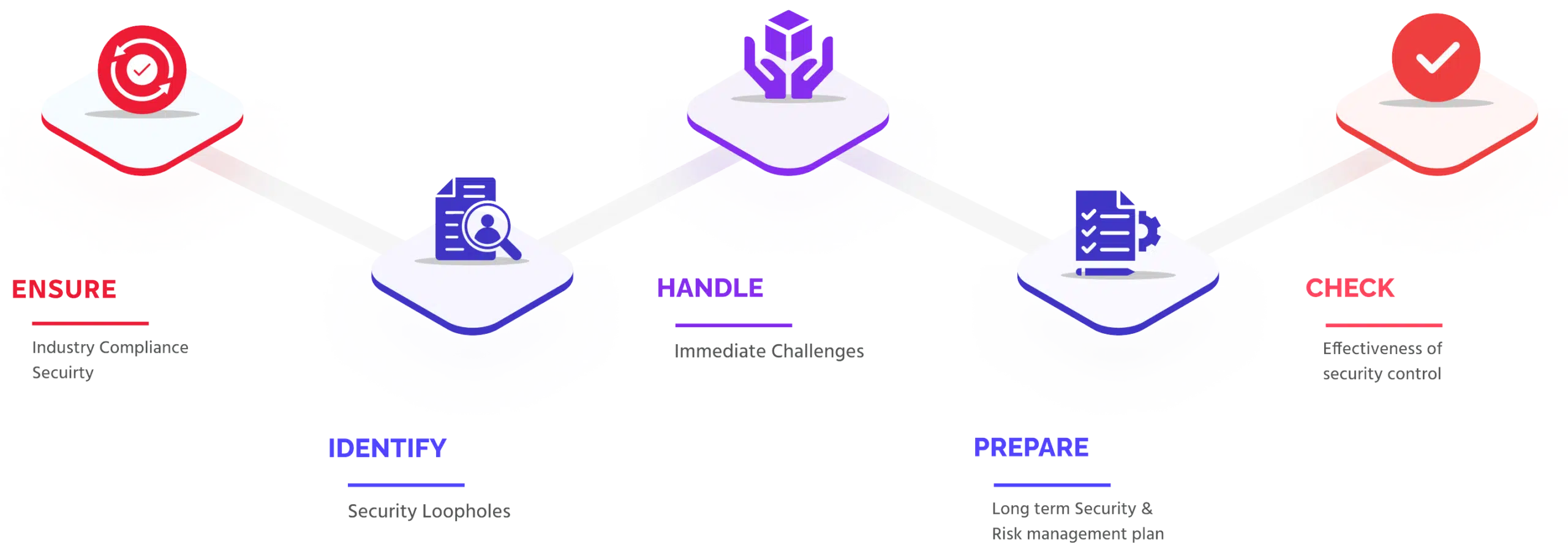
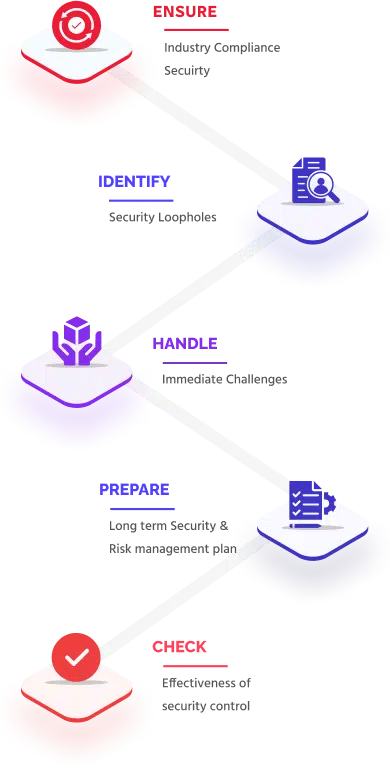
At Securityium, we’re dedicated to transforming the way you experience security testing for your business. With over a decade of experience in IT security, we understand the complex challenges companies face—from managing skilled security teams and tracking vulnerabilities to handling multiple compliance reports across industry standards. Our solution acts as a streamlined, middle layer between testing frameworks and execution, driving efficiency, effectiveness, and organization while ultimately saving you time and reducing costs in your security testing process.
Our team of experts specializes in penetration testing and vulnerability assessments, serving hundreds of companies worldwide across diverse industries. Our innovative approach to security assessments delivers tailored, reliable, and efficient solutions designed to address your unique needs. We understand the challenges of today’s digital landscape and provide the expertise you need to navigate them with confidence.