Oct 18, 2024 Information hub
Understanding the Common Vulnerability Scoring System (CVSS): A Complete Guide
The Common Vulnerability Scoring System (CVSS) is a widely adopted framework that assigns scores to security vulnerabilities, helping organizations assess and prioritize the risks posed by each flaw. It standardizes the process of measuring the severity of vulnerabilities, giving a numerical score between 0 and 10. The higher the score, the more critical the vulnerability is. By understanding CVSS and how it works, security teams can make informed decisions on which vulnerabilities require immediate attention and which can be addressed later.
In this guide, we will walk you through the key aspects of CVSS, how the scoring system works, and why it’s essential for organizations to adopt this framework.
1. What is the Common Vulnerability Scoring System (CVSS)?
CVSS is a standardized framework used to measure the severity of security vulnerabilities in information systems. It provides a numerical score between 0 and 10, allowing organizations to understand the potential impact of each vulnerability. These scores enable security professionals to prioritize vulnerability management and remediation based on the level of risk each vulnerability poses.
Key Points:
- Scores range from 0 to 10: A higher score indicates a more severe vulnerability.
- Widely adopted: It is used by companies, governments, and industries to assess risks and develop action plans.
- Prioritization tool: CVSS helps IT teams decide which vulnerabilities to fix first.
2. How Does CVSS Scoring Work?
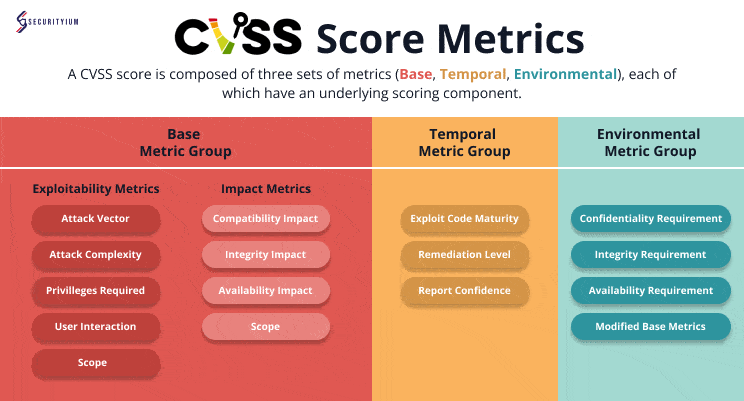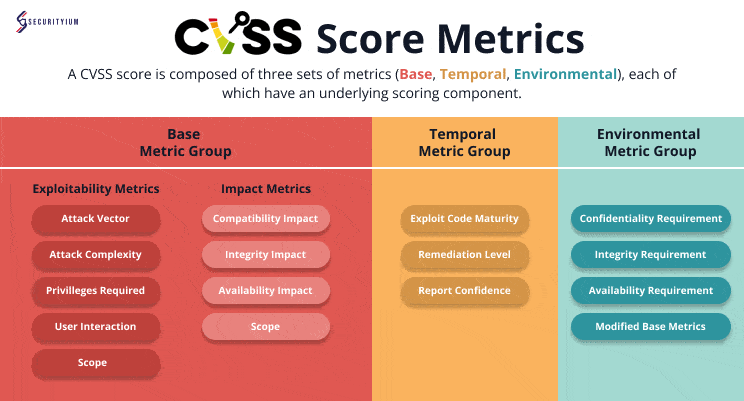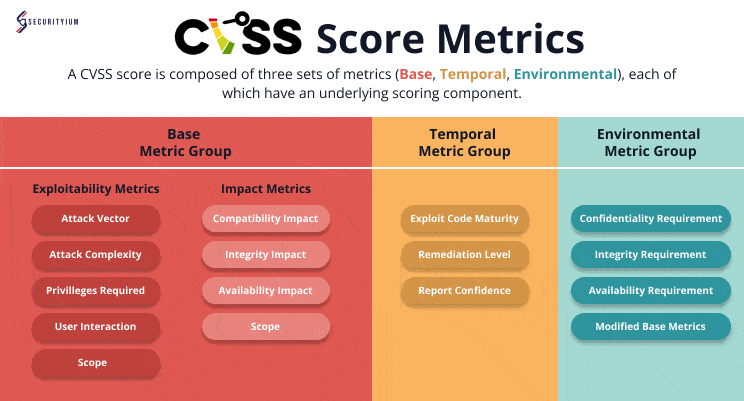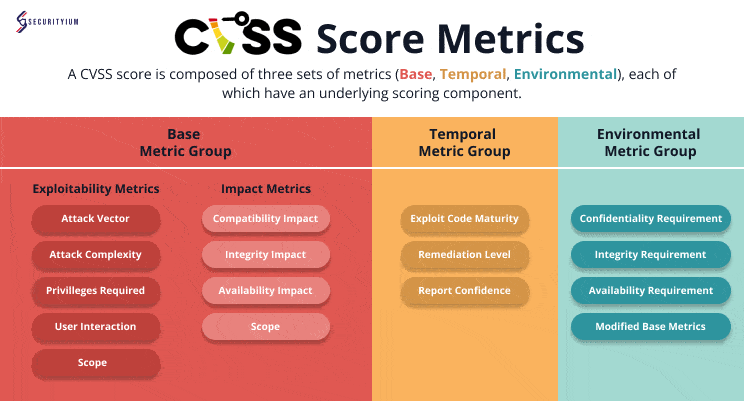
CVSS scoring is based on three types of metrics: Base, Temporal, and Environmental. These metrics combine to create an overall score that reflects both the severity of the vulnerability and the context in which it exists.
a. Base Metrics
Base metrics represent the core characteristics of a vulnerability and do not change over time. These metrics provide a starting point for understanding the inherent risk of a vulnerability.
Key base metrics include:
- Exploitability: Measures how easy or difficult it is to exploit the vulnerability. Factors like attack vector (how the attack can be launched), attack complexity (how complicated the attack is), and privileges required (level of access needed) contribute to this metric.
- Scope: Indicates whether the vulnerability affects just one system or can propagate to other systems.
- Impact: Evaluates the consequences of a successful exploit on confidentiality, integrity, and availability.
b. Temporal Metrics
Temporal metrics consider changes over time, such as the availability of patches or exploit code. This score can fluctuate as new information becomes available.
Key temporal metrics include:
- Exploit Code Maturity: Measures the development and spread of an exploit that takes advantage of the vulnerability.
- Remediation Level: Indicates whether a patch or fix is available.
- Report Confidence: Reflects the level of certainty that the vulnerability exists and can be exploited.
c. Environmental Metrics
Environmental metrics allow organizations to adjust the Base score based on their specific infrastructure and security requirements. These metrics help tailor the score to the organization’s unique risk profile.
Key environmental metrics include:
- Security Requirements: Assesses the criticality of the system affected by the vulnerability.
- Modified Base Metrics: Allows adjustments to Base metrics depending on existing mitigation measures.
Scoring Example:
Imagine a vulnerability that allows remote code execution on a web server. Its Base score might be high due to the ease of remote exploitation, but if a patch is available (Temporal metric), the Temporal score may decrease. If the server is isolated and doesn’t affect other systems (Environmental metric), the final CVSS score could be adjusted downward.
CVSS Score Table:
3. Who Should Use CVSS?
a. IT and Security Teams
Security teams and IT managers use CVSS to compare vulnerabilities and decide which ones to fix first. It simplifies decision-making by providing an objective measure of how dangerous a vulnerability is.
b. Software and Security Vendors
Application and security vendors use CVSS to prioritize vulnerability testing and remediation during software development. They ensure serious vulnerabilities are addressed before the product is shipped or updated.
c. Regulatory Bodies
Government agencies and industry bodies, such as the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), use CVSS to assess risks across industries. Compliance with CVSS-based standards is often required in industries like finance, healthcare, and retail.
d. Organizations of All Sizes
Any organization concerned with security, from large enterprises to small businesses, can use CVSS to prioritize vulnerabilities, ensuring that the most dangerous issues are fixed first.
4. Why Should Organizations Adopt CVSS?
Historically, vendors and organizations had different methods for rating the severity of vulnerabilities. This lack of standardization made it difficult to prioritize and fix security issues consistently. CVSS solves this problem by offering a common, transparent framework that anyone can use.
Key Benefits:
- Consistency: Provides a uniform method for scoring vulnerabilities.
- Transparency: Allows organizations to understand exactly how a vulnerability is rated and why.
- Prioritization: Helps security teams focus on the most critical vulnerabilities first.
- Compliance: Helps meet industry security standards, such as PCI-DSS (Payment Card Industry Data Security Standard).
Example:
Before CVSS, one vendor might rate a vulnerability as “critical” without explaining how they arrived at that conclusion. Another vendor might rate the same vulnerability as “medium” severity. CVSS offers a standardized method to avoid these discrepancies, making it easier for organizations to make informed security decisions.
5. CVSS and Its Use Cases
a. Vulnerability Management
Security teams use CVSS scores as part of a vulnerability management program. It helps them rank vulnerabilities by severity and prioritize their remediation efforts.
b. Software Development
Software developers can use CVSS scores to identify and fix serious vulnerabilities during development. It ensures that known vulnerabilities are addressed before release, reducing the risk of exploitation post-launch.
c. Incident Response
CVSS helps incident response teams understand the severity of vulnerabilities in the systems they manage. This allows them to quickly identify which vulnerabilities require immediate attention during a security breach.
d. Compliance and Auditing
CVSS plays a role in ensuring organizations comply with industry regulations. For example, unpatched vulnerabilities with CVSS scores of 4.0 or higher may affect PCI-DSS compliance, requiring businesses to address these risks to avoid penalties.
6. How is a CVSS Score Calculated?
CVSS scores are based on a mathematical formula that considers the Base, Temporal, and Environmental metrics. Although this formula can be complex, tools and calculators are available to simplify the process.
a. Base Metrics
These are fixed characteristics that determine how severe a vulnerability is, including how easy it is to exploit and the potential impact on systems.
b. Temporal Metrics
These metrics change over time, reflecting factors like the availability of a patch or the development of exploit code.
c. Environmental Metrics
These metrics vary depending on an organization’s specific setup, including the criticality of the affected system and the presence of mitigation measures.
Example:
Let’s say a vulnerability allows unauthorized access to confidential data on a web application. The Base score might be high because it’s easy to exploit remotely, and the impact on confidentiality is severe. However, if a patch has been released, the Temporal score would lower the overall risk. If the organization has strong internal controls, the Environmental score could further reduce the vulnerability’s final risk level. You can calculate the CVSS Score using the ProSecurity Portal as well.
7. CVSS Limitations
While CVSS is a valuable tool, it has several limitations that organizations must consider.
a. Limited Context
CVSS scores provide an objective measure of severity but don’t always reflect the specific risk to an organization. For example, a vulnerability that poses a severe risk to one company may be less critical for another with different security controls.
b. Subjectivity
Even though CVSS is standardized, some metrics can be subjective. For instance, how an organization assesses the Attack Complexity of a vulnerability can vary, potentially leading to different scores for the same vulnerability.
c. Limited Scope
CVSS primarily focuses on the technical aspects of vulnerabilities. It doesn’t consider other important factors, like the business impact or asset criticality, which can affect how an organization responds to a vulnerability.
d. Complexity
Understanding how to calculate and interpret CVSS scores requires expertise. For organizations without a dedicated security team, this complexity can lead to misinterpretations or misuse of the scores.
e. Oversights
Relying solely on CVSS scores may cause organizations to overlook vulnerabilities that pose a high risk but don’t score highly on CVSS. Additional methods, such as Risk-Based Vulnerability Management (RBVM), can provide a more tailored assessment by considering factors like business impact and asset value.
8. CVSS vs. CVE: What’s the Difference?
The Common Vulnerability Enumeration (CVE) and Common Vulnerability Scoring System (CVSS) are often used together but serve different purposes.
- CVE provides unique identifiers for known vulnerabilities, making it easier to track and reference them.
- CVSS assigns a score to each CVE based on its severity, giving security teams a way to prioritize remediation efforts.
Example:
The Heartbleed vulnerability (CVE-2014-0160) is one of the most famous examples of a CVE. It has a CVSS score of 7.5, indicating that it’s a high-severity vulnerability that requires immediate attention.
9. The Role of CVSS in Modern Security
Despite some limitations, CVSS remains a critical part of vulnerability management. It is widely adopted, transparent, and provides a clear framework for prioritizing security threats. However, to get the most out of CVSS, organizations should consider using it alongside other tools, such as the Exploit Prediction Scoring System (EPSS) or Risk-Based Vulnerability Management (RBVM).
- EPSS
The Exploit Prediction Scoring System predicts the likelihood of a vulnerability being exploited, helping security teams focus on vulnerabilities that are more likely to be targeted.
- RBVM
Risk-Based Vulnerability Management considers factors like asset criticality, business impact, and existing security controls to tailor vulnerability prioritization to the organization’s specific needs.
Conclusion
The Common Vulnerability Scoring System (CVSS) is a powerful tool for assessing and prioritizing security vulnerabilities. By providing a standardized score that reflects the severity of each vulnerability, CVSS helps organizations focus their remediation efforts on the most critical threats. However, it’s essential to use CVSS alongside other risk management methods to ensure a comprehensive approach to vulnerability management.
Adopting CVSS can help organizations create a consistent, transparent, and effective vulnerability management program that aligns with modern security requirements.
